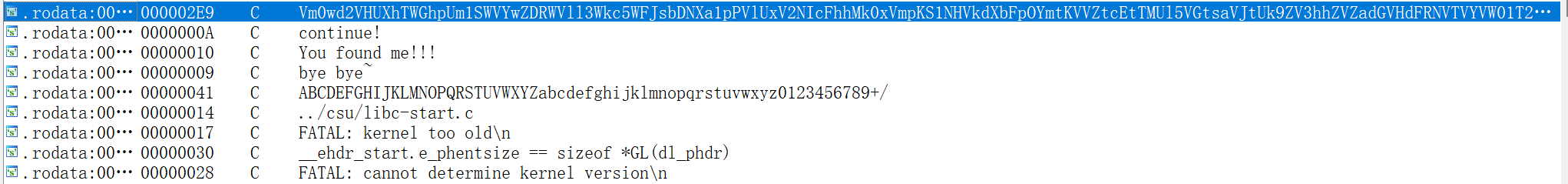
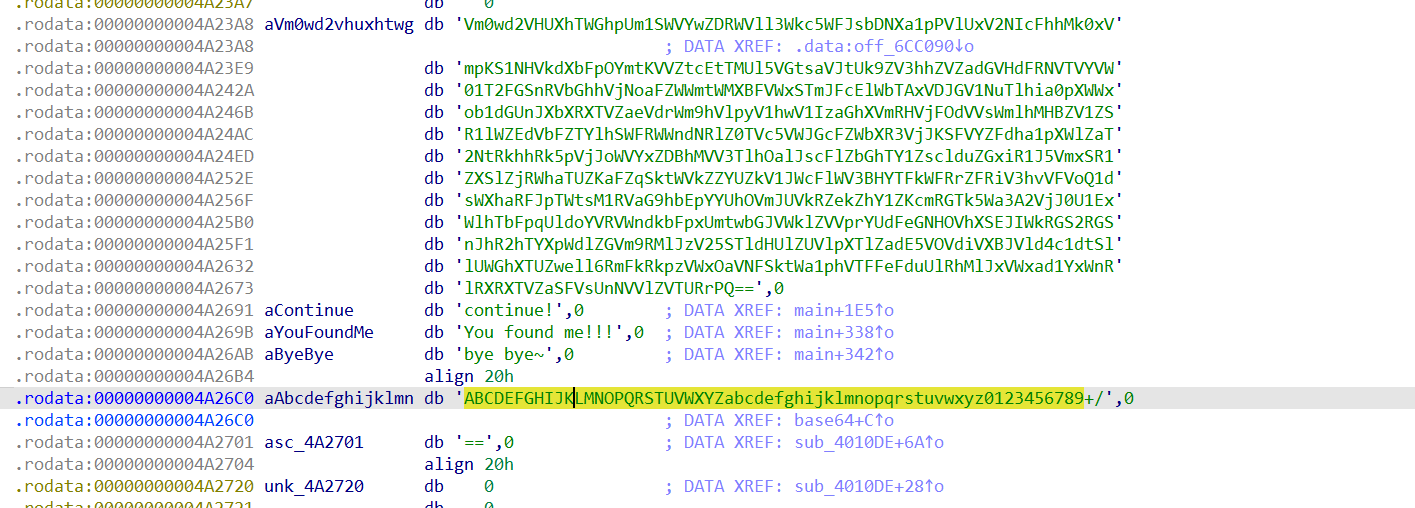
step1,通过字符串查找突破口,发现疑似base64加密的字符串,进入交叉引用查看主函数。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 int __fastcall main(int argc, const char **argv, const char **envp) { int result; // eax __int64 v4; // rax __int64 v5; // rax __int64 v6; // rax __int64 v7; // rax __int64 v8; // rax __int64 v9; // rax __int64 v10; // rax __int64 v11; // rax __int64 v12; // rax __int64 v13; // rax int i; // [rsp+Ch] [rbp-114h] char v15[13]; // [rsp+60h] [rbp-C0h] BYREF char v16[4]; // [rsp+6Dh] [rbp-B3h] BYREF char v17[19]; // [rsp+71h] [rbp-AFh] BYREF char v18[32]; // [rsp+90h] [rbp-90h] BYREF int v19; // [rsp+B0h] [rbp-70h] char v20; // [rsp+B4h] [rbp-6Ch] __int64 v21[8]; // [rsp+C0h] [rbp-60h] BYREF char v22; // [rsp+100h] [rbp-20h] unsigned __int64 v23; // [rsp+108h] [rbp-18h] v23 = __readfsqword(0x28u); qmemcpy(v15, "Iodl>Qnb(ocy", 12); v15[12] = 127; qmemcpy(v16, "y.i", 3); v16[3] = 127; qmemcpy(v17, "d`3w}wek9{iy=~yL@EC", sizeof(v17)); memset(v18, 0, sizeof(v18)); v19 = 0; v20 = 0; read(0, v18, 0x25uLL); v20 = 0; if ( strlen(v18) == 36 ) { for ( i = 0; i < (unsigned __int64)strlen(v18); ++i ) { if ( (unsigned __int8)(v18[i] ^ i) != v15[i] ) { result = 4294967294; goto LABEL_13; } } printf("continue!"); memset(v21, 0, sizeof(v21)); v22 = 0; read(0, (char *)v21, 0x40uLL); HIBYTE(v21[4]) = 0; if ( strlen(v21) == 39 ) { base64((__int64)v21); base64(v4); base64(v5); base64(v6); base64(v7); base64(v8); base64(v9); base64(v10); base64(v11); base64(v12); if ( !(unsigned int)strcmp(v13, off_6CC090) ) { printf("You found me!!!"); printf("bye bye~"); } result = 0; } else { result = -3; } } else { result = -1; } LABEL_13: if ( __readfsqword(0x28u) != v23 ) sub_444020(); return result; }
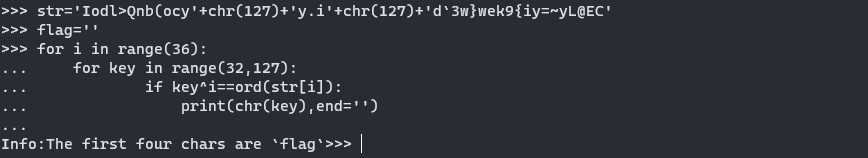
将未知的函数进行重命名,发现对字符串进行了异或处理,写个脚本运行,是个提示,flag前四个字符为flag,这不废话吗(bushi),但是后面会用到这个。
1 2 3 4 5 6 7 str='Iodl>Qnb(ocy'+chr(127)+'y.i'+chr(127)+'d`3w}wek9{iy=~yL@EC' flag='' for i in range(36): for key in range(32,127): if key^i==ord(str[i]): print(chr(key),end='') print()
我们接着对base64字符串进行解密,n次后发现是个网址,网址内并没有flag(悲):(
接着继续从字符串入手,发现了奇怪的一串,查看交叉引用
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 unsigned __int64 sub_400D35() { unsigned __int64 result; // rax unsigned int v1; // [rsp+Ch] [rbp-24h] int i; // [rsp+10h] [rbp-20h] int j; // [rsp+14h] [rbp-1Ch] unsigned int v4; // [rsp+24h] [rbp-Ch] unsigned __int64 v5; // [rsp+28h] [rbp-8h] v5 = __readfsqword(0x28u); v1 = sub_43FD20(0LL) - qword_6CEE38; for ( i = 0; i <= 1233; ++i ) { sub_40F790(v1); sub_40FE60(); sub_40FE60(); v1 = sub_40FE60() ^ 0x98765432; } v4 = v1; if ( ((unsigned __int8)v1 ^ key[0]) == 'f' && (HIBYTE(v4) ^ (unsigned __int8)byte_6CC0A3) == 'g' ) { for ( j = 0; j <= 24; ++j ) sub_410E90((unsigned __int8)(key[j] ^ *((_BYTE *)&v4 + j % 4))); } result = __readfsqword(0x28u) ^ v5; if ( result ) sub_444020(); return result; }
if ( ((unsigned int8)v1 ^ key[0]) == ‘f’ && (HIBYTE(v4) ^ (unsigned int8)byte_6CC0A3) == ‘g’ ),这不就是flag的首尾吗,可以看到循环是对v4与key[i]进行循环异或,exp如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 str='Iodl>Qnb(ocy'+chr(127)+'y.i'+chr(127)+'d`3w}wek9{iy=~yL@EC' flag='' for i in range(36): for key in range(32,127): if key^i==ord(str[i]): print(chr(key),end='') print() key= [0x40,0x35, 0x20, 0x56, 0x5D, 0x18, 0x22, 0x45, 0x17, 0x2F, 0x24, 0x6E, 0x62, 0x3C, 0x27, 0x54, 0x48, 0x6C, 0x24, 0x6E, 0x72, 0x3C, 0x32, 0x45, 0x5B, 0x00, 0x00, 0x00] key2='flag' enc='' for i in range(4): enc+=chr(key[i]^ord(key2[i])) print(enc) #enc=&YA1 for i in range(25): flag+=chr(key[i]^ord(enc[i%4])) print(flag)